Overview of the service provider SSO flow
With the Agentless Integration Kit, PingFederate includes your custom service provider (SP) application in the sign-on flow.
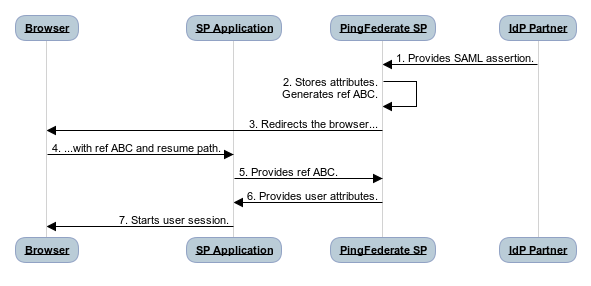
The following figure shows how your custom application is integrated into the sign-on process using the Reference ID SP Adapter:
Description
-
The identity provider (IdP) sends a SAML assertion to PingFederate.
-
PingFederate validates the assertion and temporarily captures the user-session attributes. The Reference ID SP Adapter generates a reference value (ABC). Learn more in Development considerations.
-
PingFederate redirects the browser…
-
…to the SP application with the reference value (ABC).
The reference is included in the URL query string: https://target.example.com?REF=<referenceValue>
-
The SP application sends the reference value (ABC) to PingFederate and requests the user-session attributes.
The application makes the request through an authenticated direct HTTP call to the pickup endpoint: https://pingfederate.example.com:9031/ext/ref/pickup?REF=<referenceValue>
The applications must authenticate to PingFederate using one of the three methods described in Authentication methods. If the authentication fails, the HTTP request results in an HTTP response
401 – Unauthorizedstatus code message.If you select Include Null Attributes in the adapter configuration, null attributes are included in the response from the pickup endpoint. Learn more in Reference ID SP Adapter settings reference.
-
PingFederate verifies the reference value (ABC) and returns the user-session attributes to the SP application in the HTTP response.
-
The target application uses the attributes associated with the reference value to create a user session, which allows the user to access the resource.