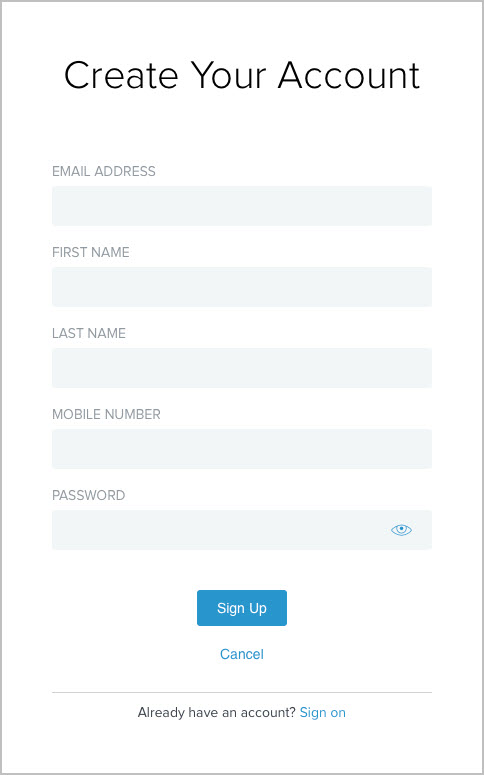
Setting up self-service registration
PingFederate leverages the HTML Form Adapter to deliver a secure and easy-to-use customer authentication, registration, and profile management solution.
About this task
A typical self-service registration setup involves five components:
For this consumer registration use case, users complete a self-service registration process to create their accounts, then access resources protected by multiple service providers.
During registration, a user provides an email address, first and last name, password, and, optionally, a mobile phone number. The email address is the user identifier. All attributes are sent to the service providers, which the partner agreements specify. You have already created a specific object class in the directory to store the user information. The object class name is aPerson, and the LDAP attributes are mail, givenName, sn, and mobile.
Steps
-
Install PingDirectory. Refer to Installing the PingDirectory Suite of Products in the PingDirectory documentation.
-
Create an authentication policy contract.
-
Go to Authentication > Policies > Policy Contracts.
-
On the Policy Contracts page, click Create New Contract.
-
On the Contract Info tab, enter a name for the authentication policy. Click Next.
-
On the Contract Attributes tab, extend the authentication policy contract by entering the
firstName,lastName,mobileNumber, andSAML_SUBJECT(email address) attributes in the Extend the Contract field.(Optional) You can add other attributes.
-
After each entry, click Add. When you are finished, click Next.
-
On the Summary tab, review your changes.
-
Click Save.
Learn more in Managing policy contracts.
-
-
Create a local identity profile using the Authentication > Policies > Local Identity Profiles configuration wizard.
-
On the Local Identity Profiles page, click Create New Profile.
-
On the Profile Info tab, enter a name in the Local Identity Profile Name field.
-
In the Authentication Policy Contract list, select the authentication policy (from step 2). Select the Enable Registration checkbox. Click Next.
-
On the Authentication Sources tab, click Next.
-
On the Fields tab, click Create New Field.
-
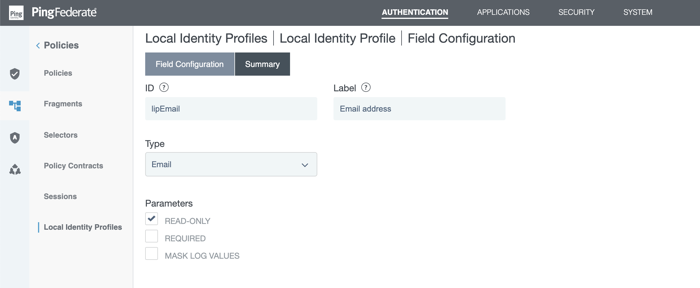
In the Field Configuration page, on the Field Configuration tab, define four local identity fields. Enter the information described in the following table.
Local Identity Profile fields and entries Type ID Label Parameters Email
lipEmail
Email address
Select the Required checkbox.
Text
lipFirstName
First name
Select the Required checkbox.
Text
lipLastName
Last name
Select the Required checkbox.
Phone
lipMobile
Mobile number
No parameters are required.
-
After each field entry, click Next. On the Summary tab, review your changes. Click Done.
-
Repeat steps 3e - 3g until the fields are entered.
As needed, select the Mask Log Values checkbox for any of the four local identity fields and Mask all OGNL-expression generated log values checkbox. The latter applies to all local identity fields.
-
On the Fields tab of the Local Identity Profile page, specify an ID field as the unique ID for your configuration and click the corresponding Unique ID. Click Next.
-
On the Email Verification tab, click Next.
-
On the Registration tab, click Next.
-
On the Data Store Configuration tab, click Configure Data Store.
-
On the Data Store tab of the Data Store Configuration page, select the LDAP datastore that been set up to connect to your PingDirectory in the Data Store list. Click Next.
-
On the LDAP Configuration tab, specify the branch of your directory hierarchy where you want PingFederate to store customer identities in the Base DN field and the LDAP attributes to be associated with fields defined in this local identity profile under Attribute.
-
On the Identity Creation tab, define the RDN pattern in the Relative DN Pattern field and select your object, such as class such as class
aPersonfor this sample use case, from the Object Class list.The pattern is as follows.
attribute1=value1[, …, attributeN=valueN]If you want to use the
${entryUUID}variable variable to guarantee the uniqueness of the relative DNs for all users, you must use it with the{entryUUID}LDAP attribute.
entryUUID=${entryUUID}-
On the Data Store Mapping tab, configure the mapping between the local identity profile fields and datastore attributes. Refer to the following table.
Mapping entries for local identity profile fields and datastore attributes Field Data Store Attribute lipEmail
mail
lipFirstName
givenName
lipLastName
sn
lipMobile
mobile
-
On the Summary tab, click Done.
Learn more in Configuring local identity profiles.
-
-
Configure an HTML Form Adapter instance for customer identities.
-
Go to Authentication > Integration > IdP Adapters.
-
Create a new HTML Form Adapter instance or reuse an existing one by clicking its name.
-
On the IdP Adapter tab in the Password Credential Validator Instance section, add the LDAP Username Password Credential Validator instance that has been set up to validate credentials stored on your PingDirectory.
-
On the IdP Adapter tab, select the newly created local identity profile in the Local Identity Profile list.
-
Complete the rest of the configuration and save all changes.
Learn more in Configuring the HTML Form Adapter for customer identities.
-
-
Create an IdP authentication policy.
-
Go to Authentication > Policies > Policies.
-
Click Add Policy.
-
On the Policy page, enter a name in the Name field.
-
Select the HTML Form Adapter instance (configured in step 4) under Policy.
-
For its Fail path, select Done.
-
For its Success path, select the local identity profile (created in step 3).
-
-
Click Local Identity Mapping underneath the selected local identity profile, which opens the Inbound Mapping & Contract Fulfillment configuration wizard.
-
On the Inbound Mapping & Contract Fulfillment Inbound Mapping page, configure the
pf.local.identity.unique.idbuilt-in local identity field for the registration process.At runtime, PingFederate fulfills the value of the
pf.local.identity.unique.idbuilt-in local identity field based on this configuration and passes the value to PingDirectory.PingDirectory uses this value to determine whether such identity has already been created. The
pf.local.identity.unique.idfield value should therefore be mapped from the subject identifier of the preceding authentication source, namely theusernameattribute from the HTML Form Adapter.For this use case, configure the Inbound Mapping page as shown in the following table.
Inbound Mapping Fulfillment Source Value pf.local.identity.unique.id
Adapter
username
-
On the Attribute Sources & User Lookup tab, click Next.
-
-
On the Contract Fulfillment tab, fulfill the authentication policy contract with values from this local identity profile as follows:
Outbound Contract Fulfillment Source Value subject
Local Identity
lipEmail
firstName
Local Identity
lipFirstName
lastName
Local Identity
lipLastName
mobileNumber
Local Identity
lipMobile
-
On the Issuance Criteria tab, click Next.
-
On the Summary tab, click Done.
-
On the Policy page, click Done.
-
Select the IdP Authentication Policies checkbox.
Other IdP authentication policies, if any, are enabled as well.
-
Click Save to retain your changes.
-
-
Map the authentication policy contract to the applicable Browser SSO connections, OAuth grant-mapping configuration, or both.
Result
You have now successfully set up self-service registration. When users sign on through this HTML Form Adapter instance, they can complete a self-service registration process to create their accounts by using the Register now link at the bottom of the Sign On page.
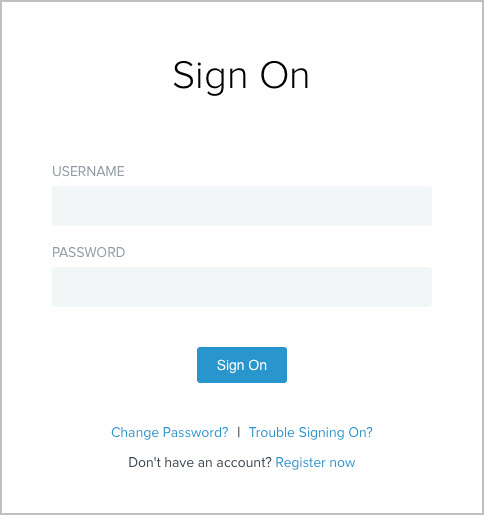
If a user chooses to register, the HTML Form Adapter redirects the user to the registration page. Based on the configuration of this sample use case as illustrated in the following registration screen capture.