Combining algorithms
Policies can combine multiple rules to produce a Permit, Deny, Indeterminate, or Not Applicable decision.
To evaluate the overall decision of a policy, the policy decision point (PDP) applies a combining algorithm. The default algorithm that is set on a new policy is The first applicable will be the final decision. If the evaluate all option isn’t selected, this algorithm stops evaluating as soon as it reaches a decision that is not Not Applicable.
The following table identifies available combining algorithms and describes their effects. The diagrams show one example of a decision evaluation for each combining algorithm; other evaluation paths are possible. The diagram legend is displayed before the table. The first column in each diagram represents the overall decision returned by the policy. The second column represents child decisions that produce the resulting policy decision.
| Combining algorithm | Details |
|---|---|
A single permit will override any deny decisions 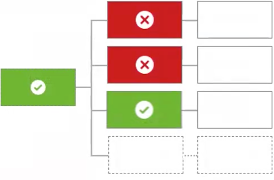
|
If any children produce the decision If no If none of the previous situations occur, the policy returns |
A single deny will override any permit decisions 
|
If any children produce the decision If no If none of the previous situations occur, the policy returns |
Unless one decision is deny, the decision will be permit 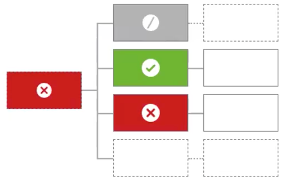
|
The policy defaults to |
Unless one decision is permit, the decision will be deny 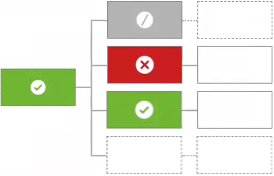
|
The policy defaults to |
The first applicable decision will be the final decision 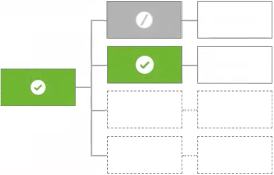
|
Evaluates the children in turn until one produces an applicable value of |
Only one child may produce a decision. If more than one is produced, the result will be indeterminate 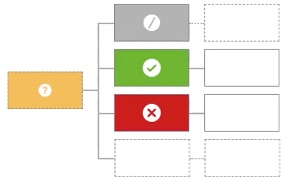
|
Evaluates the children in turn. If at any point two children produce a decision other than If exactly one child produces an applicable decision, the policy uses it. If the evaluation produces no applicable decisions, the policy returns |
Permit if the weighted average of applicable child decisions meets the threshold, otherwise deny 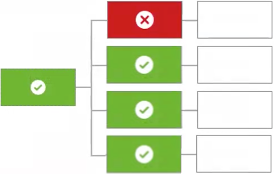
|
Assigns the policy’s children weights between After evaluating all children, the PDP divides the total by the number of children and compares that average against the threshold. If the average is greater than or equal to the threshold, the policy returns |
Evaluate all
By default, combining algorithms stop evaluating a policy’s child elements as soon as a final decision is reached. For example, when using the The first applicable decision will be the final decision combining algorithm, evaluation ends immediately if any child returns a Permit or Deny.
To override this behavior and ensure that all child policies or rules are evaluated, select the Evaluate All checkbox next to the Combining Algorithm list.
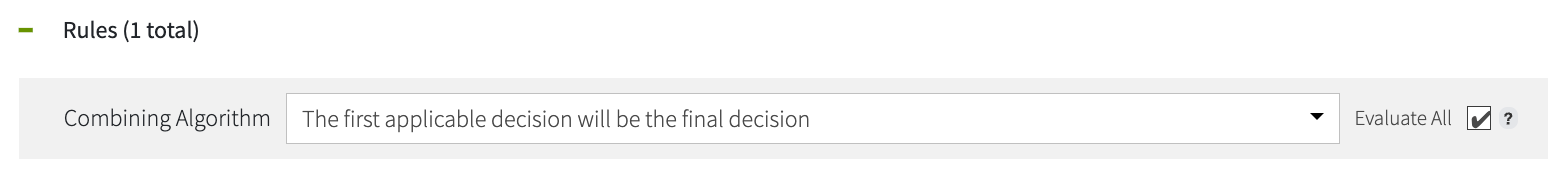
Selecting Evaluate All ensures that every child element is evaluated, even if a final decision has already been reached. Although this behavior doesn’t affect the final decision, it allows statement information, such as the reason for transaction denial, to propagate up to the parent policy. This information is useful for auditing, debugging, and understanding policy outcomes.
|
Even with Evaluate All selected, targets still determine whether a policy or rule is evaluated for a given request. |
Example: Detecting fraud with full rule visibility
Consider a bank that approves or denies transactions based on multiple risk signals. These signals are modeled as child rules under a Fraud detection policy, which uses the A single deny will override any permit decisions combining algorithm.
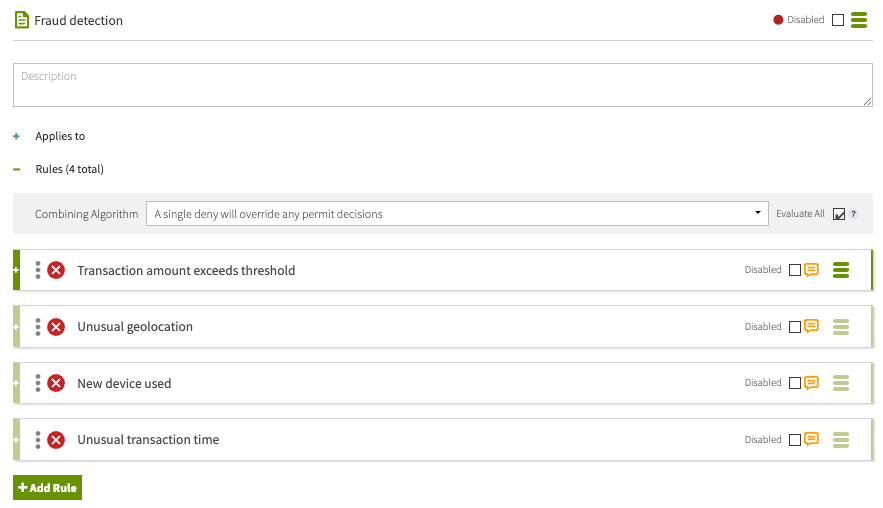
The policy includes the following rules:
-
Transaction amount exceeds threshold: Denies if the transaction amount exceeds 10,000 USD.
-
Unusual geolocation: Denies if the transaction originates from an IP or country not associated with the account.
-
New device used: Denies if the transaction comes from a device not associated with the account.
-
Unusual transaction time: Denies if the transaction occurs at an unusual time.
Each rule includes a denied-reason statement explaining why the rule denied the transaction.
With Evaluate All selected, the policy evaluates every rule, regardless of whether an earlier rule has returned a Deny. This provides analysts full visibility into every risk signal, helping detect fraud patterns, meet audit requirements, and enforce internal risk policies more effectively.
Without Evaluate All selected, the combining algorithm stops evaluating when the first Deny occurs, skipping evaluation of other potentially relevant rules. For example, if the transaction amount exceeds the threshold, the policy doesn’t evaluate the geolocation or device rules, and their corresponding denial reasons aren’t included in the final decision.