Configuring an authentication claim for the Microsoft 365 application
If you set up a Microsoft 365 application to connect to a Microsoft Entra ID domain, PingOne is the federated identity provider (IdP) for users of the domain, and Entra ID redirects users to PingOne for authentication.
When users complete multi-factor authentication (MFA) with the federated IdP, such as PingOne, Entra ID expects the IdP to send an MFA claim to Entra ID to communicate that authentication has been completed. Add an MFA claim in the Microsoft 365 application in PingOne for Entra ID to consider MFA fulfilled.
|
An external authentication method in Entra ID isn’t required when the users reside in an Entra ID federated domain. |
Before you begin
-
Add Microsoft 365 to the application catalog and and complete the PowerShell cmdlets to set up PingOne as the federated IdP for the domain in Entra ID. Learn more in Adding Microsoft 365 to the PingOne application portal.
-
Review Using WS-Fed or SAML 1.1 federated IdP in the Entra ID documentation.
Steps
-
In the PingOne admin console, go to Applications > Applications and click the Microsoft 365 application in the Applications list.
-
On the Attribute Mappings tab, click the Pencil icon.
-
Add a new attribute for the authentication method:
-
Click + Add.
-
In the Attributes field, enter
authenticationmethod. -
Click the More Options (⋮) icon and click Update NameFormat.
-
In the NameFormat list, select http://schemas.microsoft.com/ws/2008/06/identity/claims.
-
Click Update.
-
Click the Gear icon to open the Advanced Expression modal.
-
Enter
"http://schemas.microsoft.com/claims/multipleauthn"(with the quotation marks).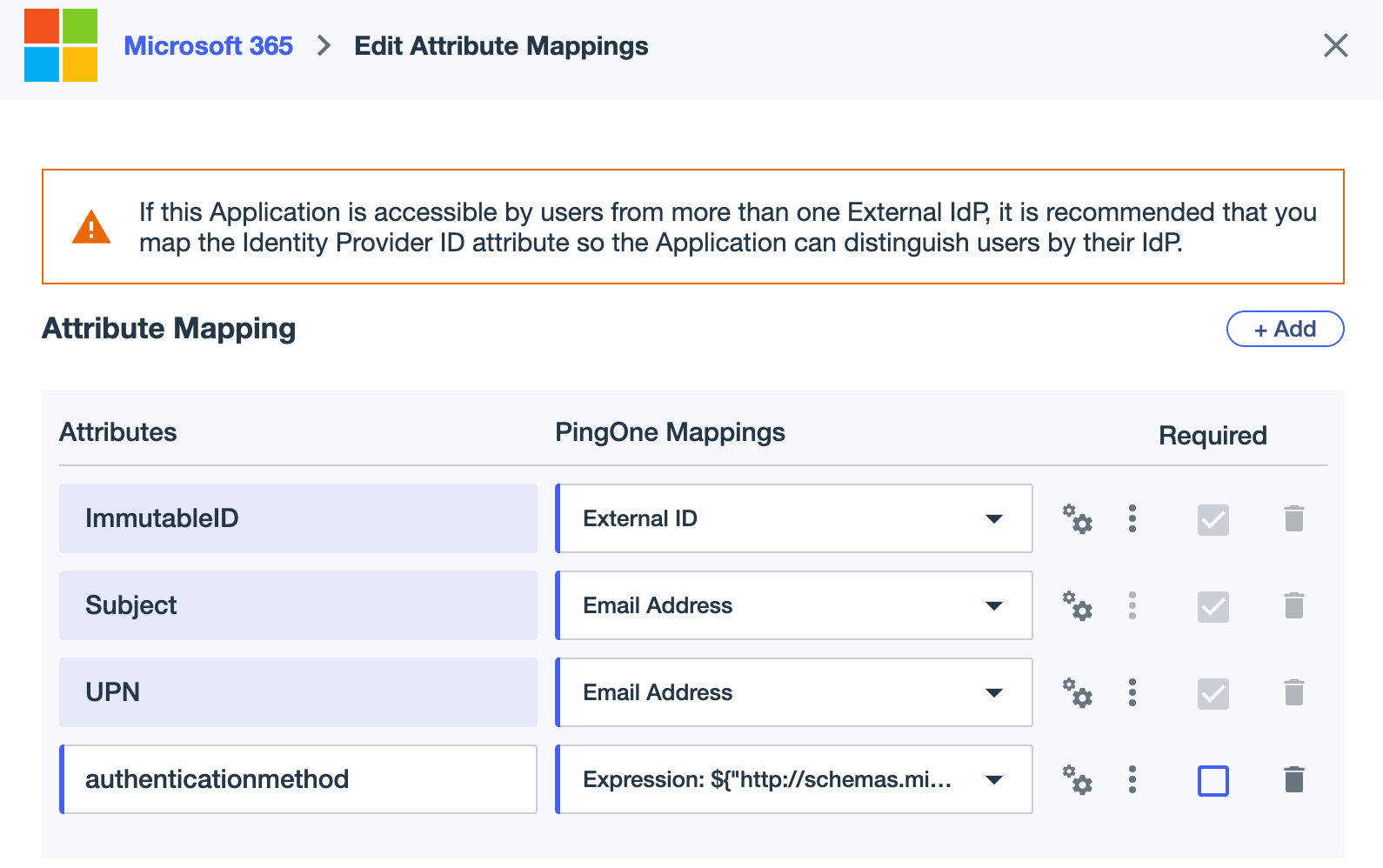
-
Click Save.
-
-
On the Attribute Mappings tab, click Save.